Building a WordPress SOC: Tools, Setup, and Operational Security (OpSec) Essentials
When we kicked off the latest WooCommerce Meetup, we wanted to do something a bit different. Instead of sticking to conversion rates and checkout UX (the usual eCommerce suspects), we went under the hood of WordPress security – where outdated plugins, weak passwords, and lazy permissions can quietly wreck a shop.
“WordPress is insecure.” We hear that at every meetup, in every sales call, and in at least three Slack threads a week. The reality is less dramatic and more actionable. Most breaches come from stale plugins, weak passwords, sloppy permissions, and partners who treat security like a footnote. That was the point of Matko Antun Bekavac from Offset Concepts and Hero Factory at our WooCommerce Meetup. He has lived on both sides of the fence, from building eCommerce systems to breaking them in controlled conditions, and he showed us how a real attacker enumerates, exploits, and persists on a typical shop.
We are not interested in platform wars. We care about what you can fix on your store by next Tuesday. WordPress still powers a huge slice of the internet, and WooCommerce runs a meaningful chunk of eCommerce. That reach attracts attackers, but it also means the playbook for defense is well known. In his talk, Matko walked through the exact tools and habits that move the needle, from WPScan recon to boring but essential controls like patching cadence, MFA, and least privilege.
How attackers think about your shop
Matko structured the offensive side around a simple loop: enumerate, exploit, persist.
- Enumerate what is exposed
Attackers fingerprint your stack and versions, enumerate users, and map plugins and themes. Tools like WPScan make this easy. Even the free tier’s API is enough to surface vulnerable components and usernames in many configurations - Exploit the first weak link
Common wins line up neatly with the OWASP Top 10: broken access control, injection flaws, cryptographic failures, vulnerable components, and security misconfiguration. If an old plugin or theme exposes a known CVE, that is usually the door. - Persist quietly
Once in, the goal is to stick around. On WordPress this often means slipping malicious code into a child theme’s functions.php or another file that will not be touched by routine updates. If nobody monitors file integrity, persistence can last months.
Most compromises start from things you can control: patch cadence, credential hygiene, rate limiting, and least-privilege access.
Why this matters even more in 2025
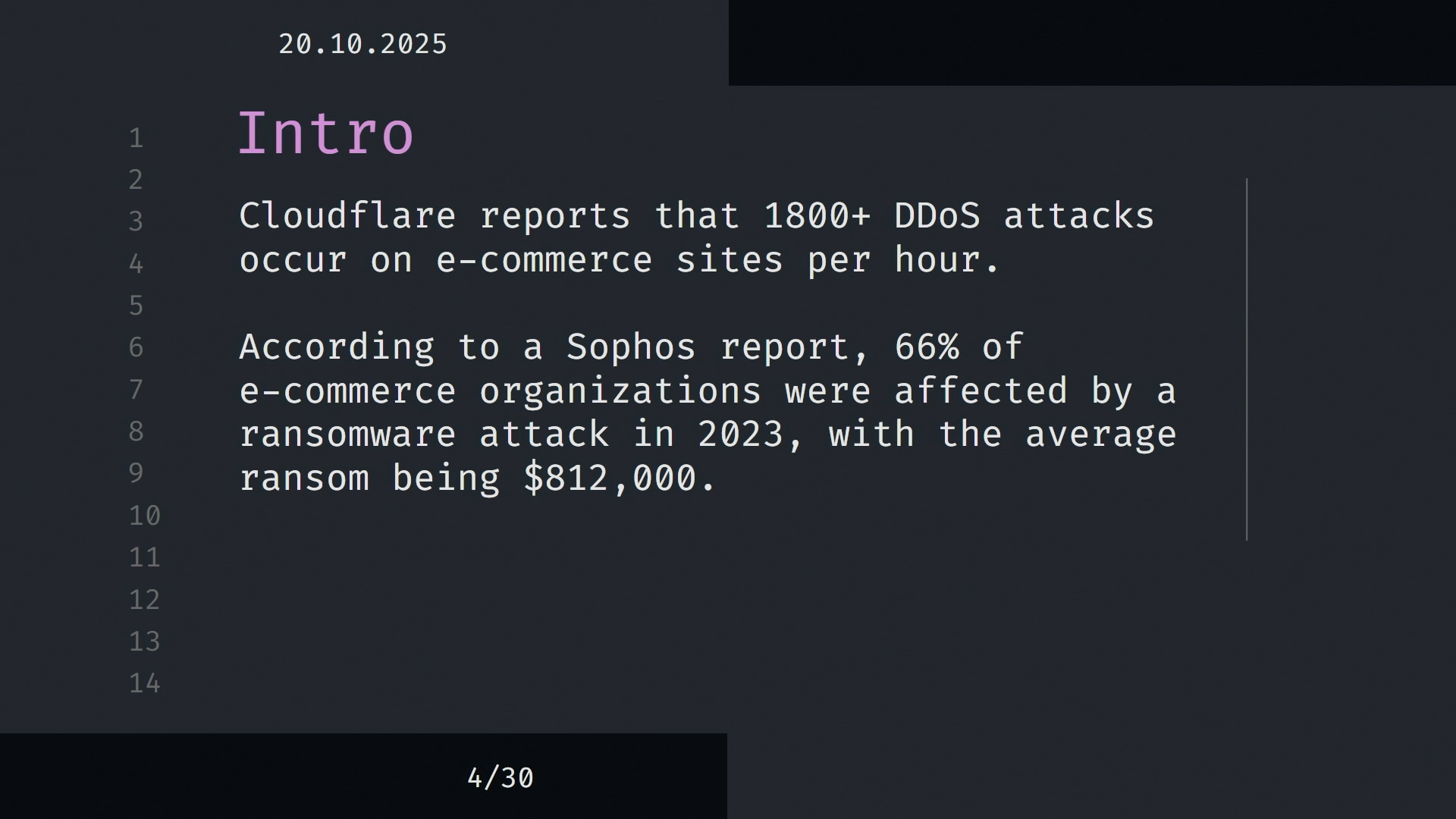
Attackers are not just bored teenagers. Bot traffic and automation make it trivial to hammer weak targets at scale. Recent reports show automated traffic and “bad bot” activity rising and, in some sectors, overtaking human traffic. That includes API-first attacks on retail and financial services. And when someone decides to simply take you offline, DDoS attacks are scaling into the double-digit terabits per second. That is not theoretical; it is actively being mitigated on the open internet.
For eCommerce, that translates to two kinds of losses: the quantifiable (missed orders) and the intangible (trust).Matko spun up a fresh Kali install and showed a typical recon chain. With WPScan, he enumerated usernames and outdated components, then demonstrated how a simple dictionary brute-force on a known user can still succeed if there is no rate limiting or MFA on /wp-login.php. He also walked through how vulnerable plugins and year-old themes can cascade into privilege escalation or remote code execution if patching is neglected. Nothing exotic, just the kind of workflow any persistent attacker or bot farm can reproduce.

Defense that actually works on WooCommerce
Here is the part we love, because it is the boring stuff that saves real money.
1) Update like you mean it
Keep core, plugins, and themes current. Replace abandonware. If an extension is business-critical, pick a vendor with a track record of timely security releases.
2) Reduce your attack surface
Remove unused plugins, disable XML-RPC if you do not need it, and lock down /wp-admin with IP allowlists where feasible.
3) Stop credential bingo
Enforce MFA for all admins and editors. Require unique, long passwords via a manager. Add rate limiting and lockouts to /wp-login.php and any SSO endpoints. Do not expose admin on the default path if you can avoid it.
4) Treat “known vulns” as incidents
Schedule weekly vulnerability scans. WPScan’s API limits are enough for most small properties, and paid scanning or a managed service is justified for larger fleets.
5) Monitor file integrity
Alert on changes to wp-content, especially child theme directories and functions.php. Keep a clean checksum baseline and compare on deploy.
6) Least privilege, always
Map roles to tasks. Editors should not be admins. Partners should not inherit your crown jewels. Rotate credentials when people leave.
7) Backups that actually restore
Use versioned, immutable, offline backups. Test restores quarterly. If ransomware ever lands, this step is the difference between downtime and disaster.
8) Prepare for DDoS
Sit your site behind a network that can absorb modern surges. Cloud-scale providers publish what they mitigate per hour for a reason. Build your plan to that bar.
9) Know your frameworks
Use the OWASP Top 10 as your baseline checklist for reviews. Layer in CIS Critical Security Controls and MITRE ATT&CK for process, detection, and threat-informed defense. These three cover most org sizes without reinventing the wheel.
10) Verify partner hygiene
If an agency or integration partner gets popped, you get popped. Do due diligence up front: ask for their patch policy, incident process, MFA requirements, and how they segregate client access.
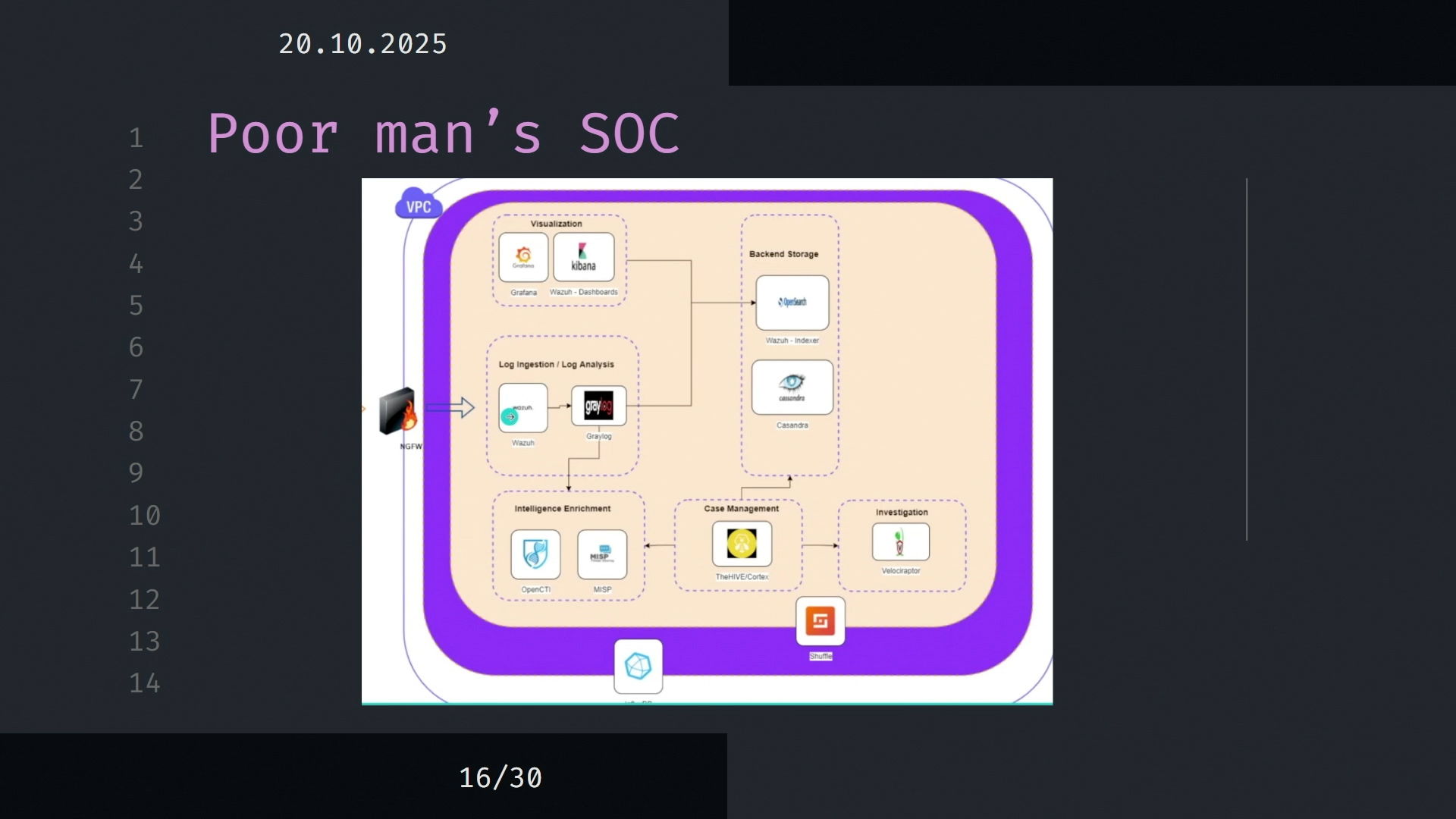
A SOC on a shoestring
One of Matko’s most memorable ideas was what he calls the “social SOC”: a security operations center you can actually afford. Forget the enterprise setups that cost €10,000 a month. With a bit of curiosity and open-source spirit, you can build serious visibility for the price of a Friday pizza run.
His toolkit reads like a hacker’s grocery list:
- Wazuh for endpoint monitoring and log collection,
- OpenSearch or Graylog to index and query events,
- Grafana or Kibana to visualize what’s happening under the hood,
- MISP and OpenCTI to feed you real-time threat intelligence,
- TheHive and Cortex for incident triage, correlation, and enrichment.
It’s modular, transparent, and best of all – yours to control! You won’t rival a 24/7 managed security provider overnight, but you will spot the early warnings: file tampering, brute-force flurries, or a rogue plugin update gone sideways.
Final thoughts: No silver bullets, just good hygiene
Matko’s talk was a reminder that real security comes from tried and true habits, not superficial hype. For anyone building WooCommerce stores, that’s the point worth remembering. And you don’t need fancy badges or a five-figure security budget to get there.
At Neuralab, we’ve spent years stress-testing shops and our own nerves in the process. Security is a team sport and we’re always looking for teammates who think the same way. If you want to turn Matko’s playbook into action, harden systems that millions rely on, and still have fun debating WordPress hooks over coffee, check out our LinkedIn job post. We’re hiring a WordPress engineer who loves open source, teamwork, and the occasional existential code review.